We are offering the following services:
1. Virtualization Solutions:
Virtualization technologies are present from 1960s onwards and in the last two decades has impacted almost all aspects of IT Industry. It has impacted Storage, Network, Processing Power technologies and paved the way for totally new companies and saved lot of money, time to the Organizations. What was not possible previously is now possible and all thanks to Virtualization technologies.
Server Consolidation, Desktop Virtualization, Network Virtualization and Storage Virtualization are the new pillars of the Organization. Computer Port IT Solutions render the solutions on all the above technologies.
2. Cloud Solutions:
Again, the fundamental building block for the Cloud Platform is Virtualization and Cloud Solutions can bring substantial savings to any Organization, be it Public Cloud or a Private Cloud or even a Hybrid Cloud.
3. Security Solutions:
The importance of Security Solutions has increased particularly in the last 3-4 years mainly due to the magnitude and sharpness of all the threats. The severity of the threats is quite dangerous as syndicated Organizations and sometimes rogue countries are behind the meteoric rise of these threats. Ransomware is robbing the Organizations across the World and unless solid counter measures are not in place, more Organizations are going to lose not only critical data but also the reputation
4. Mailing Solutions:
Mailing Solutions are considered as the defacto service by the employees of any Organization. With advent of Cloud Solutions, Mailing solutions combined with Instant Messaging and Video, Audio Conferencing are common and most of the employees and also the suppliers are demanding for this service. Plain email is considered as a passé and new age features like sharing of large documents with links, video and audio collaboration are demanded. Mail archiving solutions are also required for Organizations because of various reasons like compliance, retention of knowledge, for legal purposes etc.,
5. DR Solutions:
Disaster Recovery Solutions for all critical applications is a must now a days as the downtime is not being accepted by users or the management. Any downtime can impact the business transactions and in this age of aggressive competition, downtime is not an option. So, all critical applications need a High Availability and Disaster Recovery Strategy.
6. Storage Solutions:
Storage requirements are growing by more than 100% year on year. The amount of data - both structured and unstructured created is doubling for every 5 years. The market is expecting the Organizations to keep large amounts of data due to compliance and also this data if kept by the Organizations can be used to churn large amounts of meaningful business by doing a research on the patterns.
Software Defined Storage Solutions help the Organizations to keep the data intact with hierarchical storage systems which will reduce the costs that are involved in maintaining it. SDS can help the Organizations in Block, File and Object Storage systems.
Also, SDS Solutions involve HCI (Hyper Converged Infrastructure) Solutions which will help in reducing the costs and also Organizations can scale horizontally. Most of the NAS boxes and SAN boxes cannot scale horizontally and this will create islands of information which are difficult to bridge.
Implementing a Hyper Converged infrastructure solution (SDS solution) can pay back in less than a year for the Organizations.
7. SD-WAN Solutions:
Connectivity is the life line for any Organization having offices across multiple cities or countries. The only reliable solution since last one decade is the implementation of MPLS Networks. MPLS is a reliable technology but due to the increased reliability of cheap Internet connections, it is now possible to take 2-3 broadband connections and this coupled with SD-WAN technology will give the same sort of reliability as that of MPLS and also save substantial amount of money. Apart from this, with MPLS implementation, it is always vendor lock-in and any changes in the bandwidth cannot be implemented fast and there will be some feasibility issues with the locations.
SD-WAN solutions can bring lot of advantages to the Organizations like - faster rollout, usage of cheap and reliable broadband and Internet Leased lines (aggregation of links),Quality of Service (QoS) can be guaranteed for critical services like Video Conferencing, Audio Conferencing and important applications.
8. Identity Access Management Solutions:
With multitude of applications that are being used by Enterprises, it is essential for the security of the applications and also Single Sign-on to these applications.
9.OpenNebula
OpenNebula provides the most simple but feature-rich and flexible solution for the comprehensive management of virtualized data centers to enable private, public and hybrid IaaS clouds. OpenNebula interoperability makes cloud an evolution by leveraging existing IT assets, protecting your investments, and avoiding vendor lock-in.
OpenNebula is a turnkey enterprise-ready solution that includes all the features needed to provide an on-premises (private) cloud offering, and to offer public cloud services.
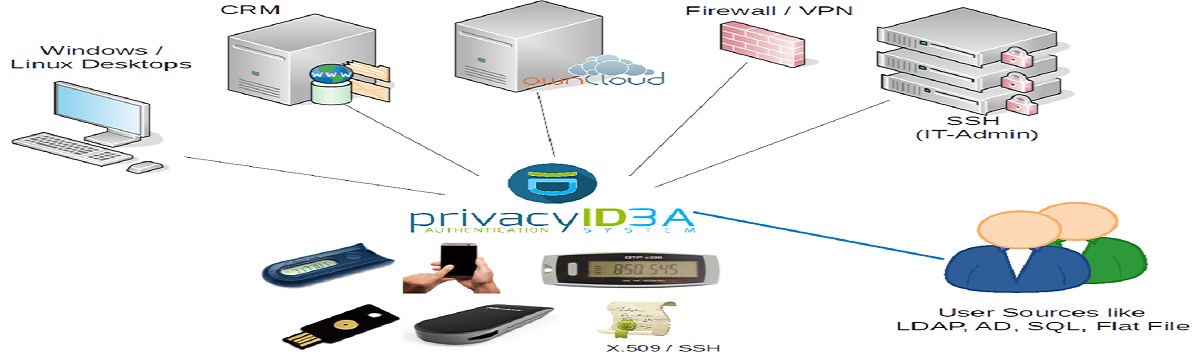
10.2FA/OTP (Second Factor Authentication / One Time Password)
Two-factor authentication (also known as 2FA) is a type (subset) of multi-factor authentication. It is a method of confirming a user's claimed identity by utilizing a combination of two different factors: 1) something they know, 2) something they have, or 3) something they are.
A good example of two-factor authentication is the withdrawing of money from an ATM; only the correct combination of a bank card (something that the user possesses) and a PIN (personal identification number, something that the user knows) allows the transaction to be carried out.
Two-step verification or two-step authentication is a method of confirming a user's claimed identity by utilizing something they know (password) and a second factor other than something they have or something they are. An example of a second step is the user repeating back something that was sent to them through an out-of-band mechanism. Or the second step might be a 6 digit number generated by an app that is common to the user and the authentication system
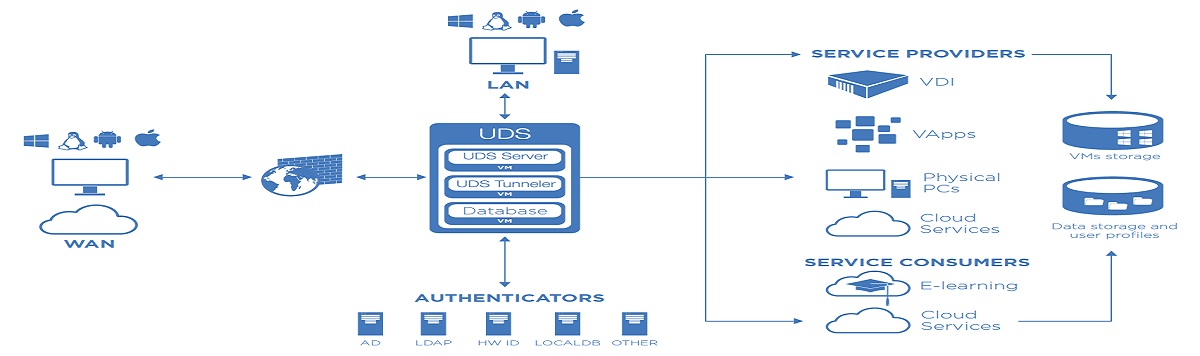
11.VDI & App Virtualization Solution
Quick and easy to deploy unlimited remote desktop services, VDI, applications, Physical PCs, e-Learning, cloud services and much more.
Multiple hypervisors, authenticators and connection protocols
Windows & Linux OS
With UDS, it is easy to setup Desktop Virtualiation and App Virtualization
12.SSO (Single Sign-On)
Single sign-on (SSO) is a property of access control of multiple related, yet independent, software systems. With this property, a user logs in with a single ID and password to gain access to a connected system or systems without using different usernames or passwords, or in some configurations seamlessly sign on at each system. This is typically accomplished using the Lightweight Directory Access Protocol (LDAP) and stored LDAP databases on (directory) servers. A simple version of single sign-on can be achieved over IP networks using cookies but only if the sites share a common DNS parent domain.
For clarity, it is best to refer to systems requiring authentication for each application but using the same credentials from a directory server as Directory Server Authentication and systems where a single authentication provides access to multiple applications by passing the authentication token seamlessly to configured applications as Single Sign-On.